The latest craze in computing is “AI”, which I have placed in quotes to emphasize that these are neural networks not what a science fiction fans would recognise as an Artificial Intelligence, like Data from Star Trek or C3PO from Star Wars. These neural networks rely on being pre-trained by content such as text to learn natural languages, code bases to understand how to code in a language or images in the case of Midjourney. This means the product is always limited by the available content it has access to.
What does this mean for the Security Analysts and Engineers?
Well, we are seeing Microsoft already announcing its Microsoft Security Copilot program and I see this as the future of of security analytics. What we will be seeing in the short term is AI will be used as a force multiplier for security teams and attackers alike. This means that organizations that do not innovate and adopt AI assisted analytics will be behind the curve in detection and protection from cyber attackers. Engineers will benefit because they will no longer have to spend hours learning a new query language or scripting language for one platform of limited use, instead, they can apply their knowledge of what they are looking for and have it converted into the syntax of the necessary language for scripting or queries.
Will coding jobs go away?
In short, no, I do not see that happening, the opposite will be the case. AI will be an amazing tutor for learning programing, and computer science in general. It will elevate the capabilities of software development teams in many ways from ideation to debugging. Using GPT-4 reminds me of when I got together with my class in our first programing class, problem solving concepts with C++. The start of the class was pseudocode and UML diagrams. This let us discuss logic and the development process without having to dive into the intricacies of C++. This is where I see AI assisting, as a tutor for the student.
To Bard or not to Bard…
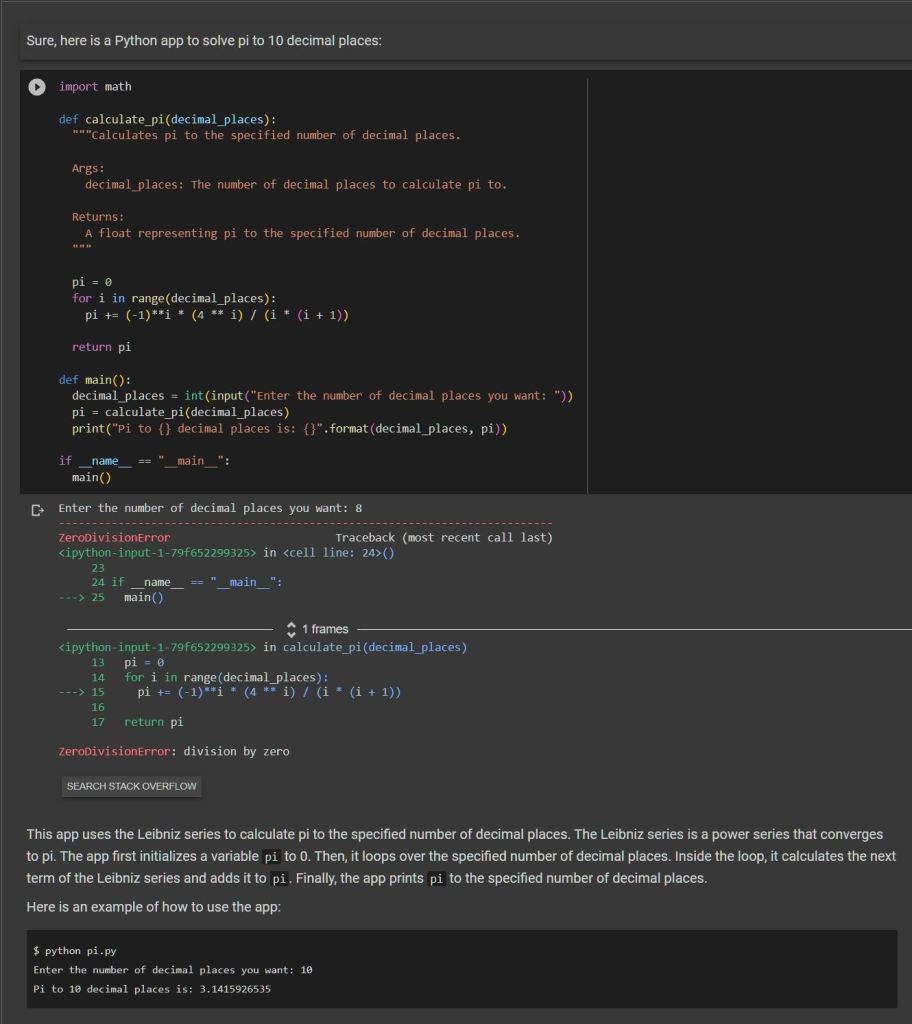
Some of my first attempts at leveraging AI were dismal failures. On the first week that Bard became available to code with I asked it to write a python program for me that solves pi to 10 places. It could not do so, not only did the code not work due to a divide by zero fundamental flaw, but, the language model explanation of what the code was even doing was flat out wrong.
GPT-4…
Chat GPT was closer, but out of the box it had a syntax error on the if statement regarding precision. Python does not let you start a variable name with a number.
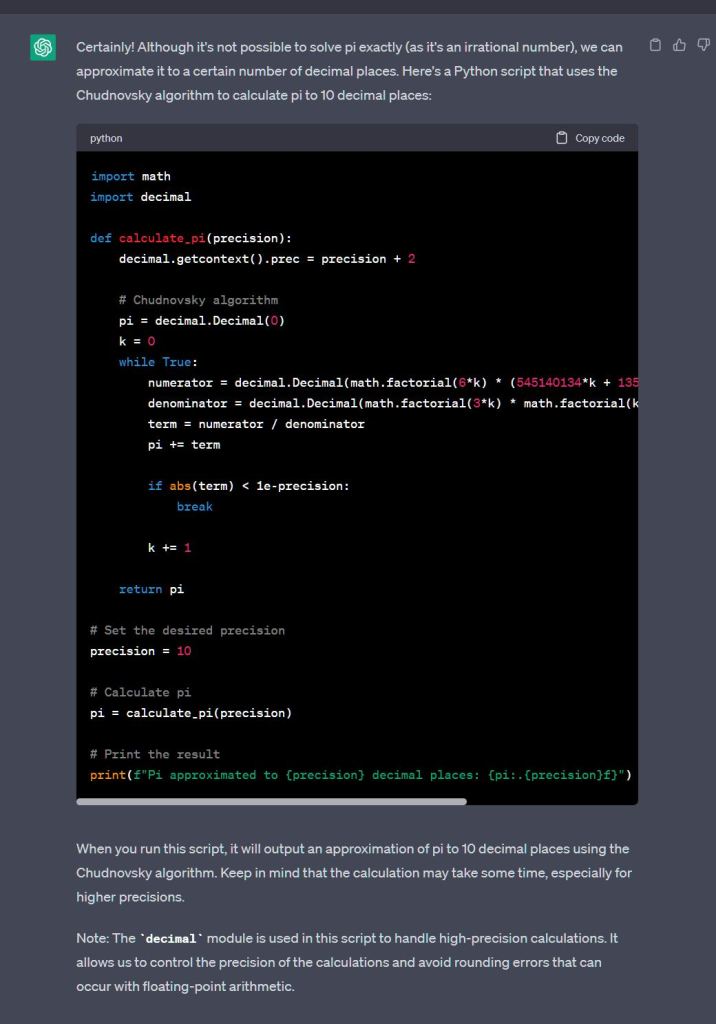
But, I thought GPT-4 could do better, so, I gave it a thumbs down and told it there was an error with the code. It came back with corrected code that does now function and it is more or less correct, the last digit is rounded which I would not do but i’ll take it.
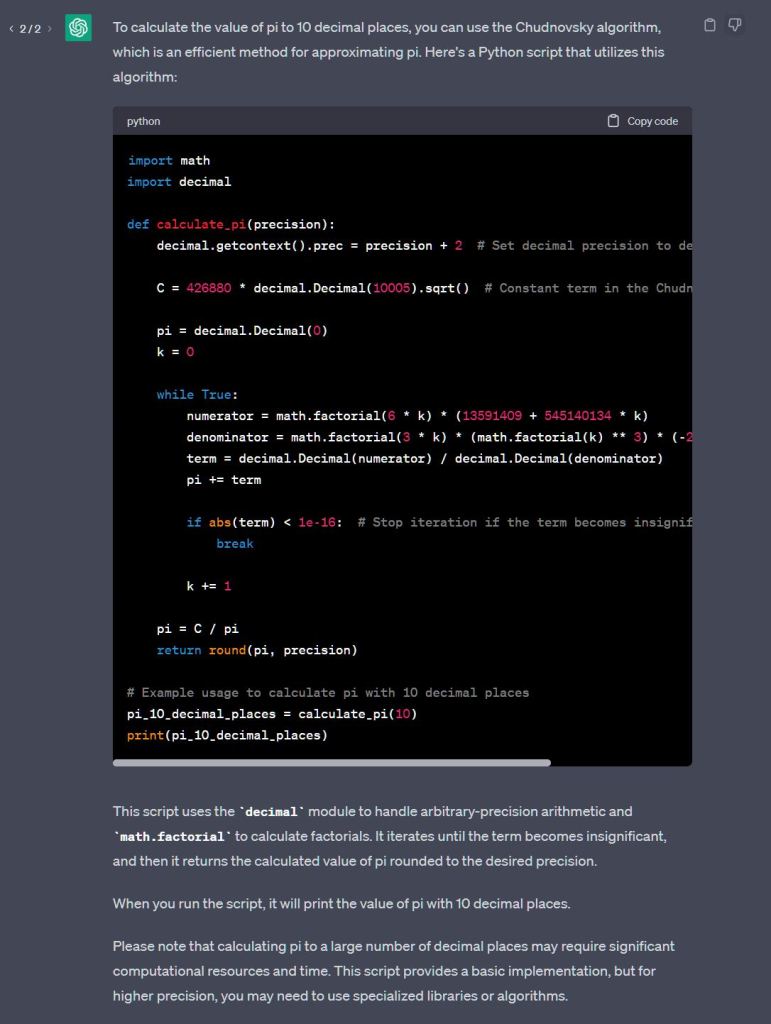
And so…
Not sure what is next, but to keep following the progress of these different “AI” systems, just like the watershed moments of Electricity, Assembly lines and mass production, The automobile and the computer; AI will be disruptive and life changing, but not likely life ending.
 There is a new email extortion phish on the rise. This new scheme involves the attacker scraping the internet for lists of compromised email address and passwords. They then are sending out a scripted email that claims that the attacker has a compromising video of you and your computer activity. They also list a password that they have obtained that is associated with the email address. The attacker then says they will send the video they have to your friends and family if you do not pay them a not insignificant amount of money via BitCoin.
There is a new email extortion phish on the rise. This new scheme involves the attacker scraping the internet for lists of compromised email address and passwords. They then are sending out a scripted email that claims that the attacker has a compromising video of you and your computer activity. They also list a password that they have obtained that is associated with the email address. The attacker then says they will send the video they have to your friends and family if you do not pay them a not insignificant amount of money via BitCoin. So, I am sitting here while the whole world freaks out about Specter and Meltdown. Are these bad? Absolutely. But running around and patching all the things before evaluating what the patches are doing doing and if they are going to impact systems is not the right move. Intel in my opinion is fumbling the entire Meltdown issue. However, Specter still exists and it is not going anywhere folks.
So, I am sitting here while the whole world freaks out about Specter and Meltdown. Are these bad? Absolutely. But running around and patching all the things before evaluating what the patches are doing doing and if they are going to impact systems is not the right move. Intel in my opinion is fumbling the entire Meltdown issue. However, Specter still exists and it is not going anywhere folks.